Introduction to Computer Forensic Investigations
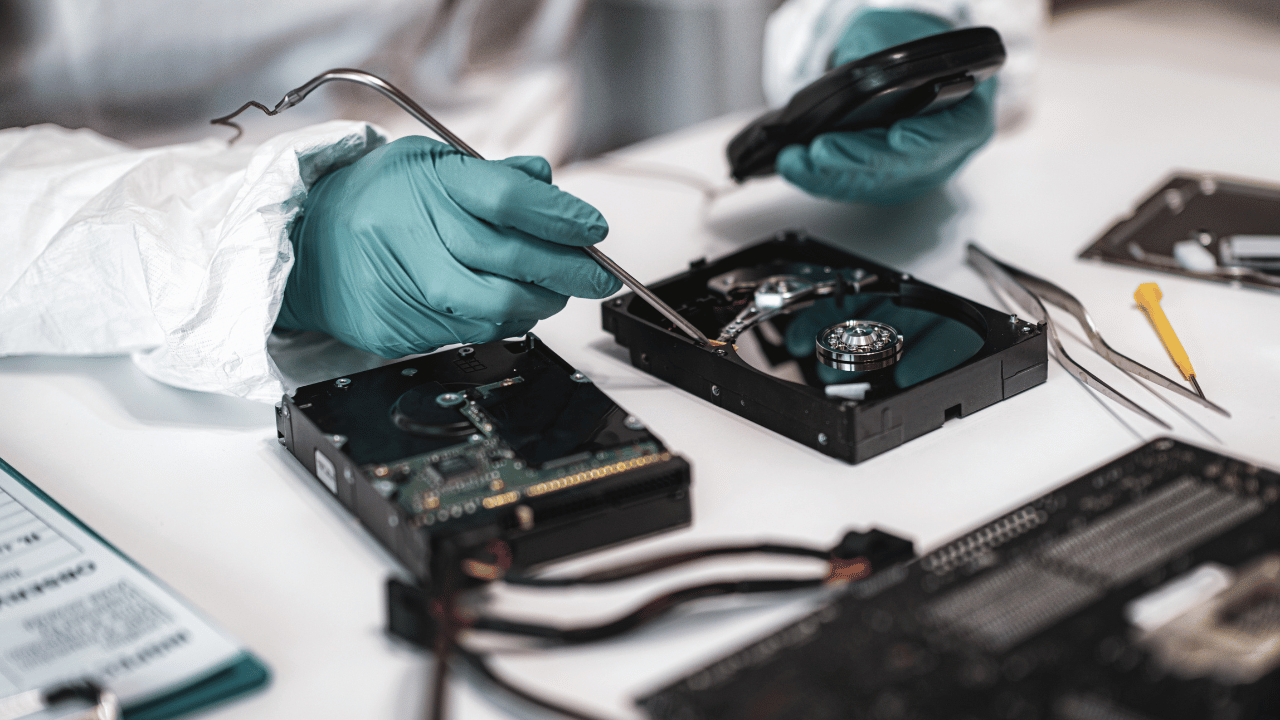
The Role of Computer Forensics in Cybersecurity
Navigate through the intricacies of file systems from a forensic standpoint. Gain insights into how forensic investigators analyze file structures, recover deleted data, and piece together the digital puzzle to reconstruct events.
Forensic Tools of the Trade: A Comprehensive Overview
Legal and Ethical Considerations in Computer Forensics

Strengthening Password Policies: A Crucial Line of Defense
Illustrate the practical application of computer forensic techniques through real-world case studies. Analyze notable examples where forensic investigations played a pivotal role in solving cybercrimes and addressing digital security breaches.
Emerging Trends and Future Challenges in Computer Forensics
Anticipate the future of computer forensics by exploring emerging trends and potential challenges. Stay ahead of the curve with insights into evolving technologies, new investigative methodologies, and the continuous adaptation required in the dynamic field of computer forensic investigations.

